In H1 2025, crypto users lost $2.3 billion, with $340 million tied to
social engineering scams alone. As per a Cointelegraph update, Discord “try-my-game” traps, which drained an NFT artist for $170,000, and fake AI or gaming startups using polished Notion pages and verified X accounts to spread wallet-stealers show how fast these schemes evolve.
Zoom out, and the numbers get starker. Chainalysis reported that $40.9 billion in illicit crypto flows were tracked in 2024, though just 0.14% of on-chain activity is criminal. That small share still translates into massive losses, and in a
bull market it grows fast. The 2025 crypto rally won’t just mint winners, but it will also fuel human-targeted fraud like deepfakes, blind-signing drains, and executive impersonation unless users know the red flags and tighten their defenses.
Below you’ll find the top social engineering scams to watch, real examples, red flags, and the exact steps to protect your crypto assets, on BingX and beyond.
What Is a Social Engineering Crypto Scam and How Does It Work?
A social engineering crypto scam is a type of cryptocurrency fraud where scammers target people instead of blockchains or smart contracts. Rather than breaking code, they use psychological manipulation by pretending to be trusted figures, creating fake urgency, or exploiting community trust to trick victims into revealing private keys, passwords, or sending funds.The goal is to get you to click a malicious link, download fake software, or approve a risky on-chain transaction that drains your wallet.
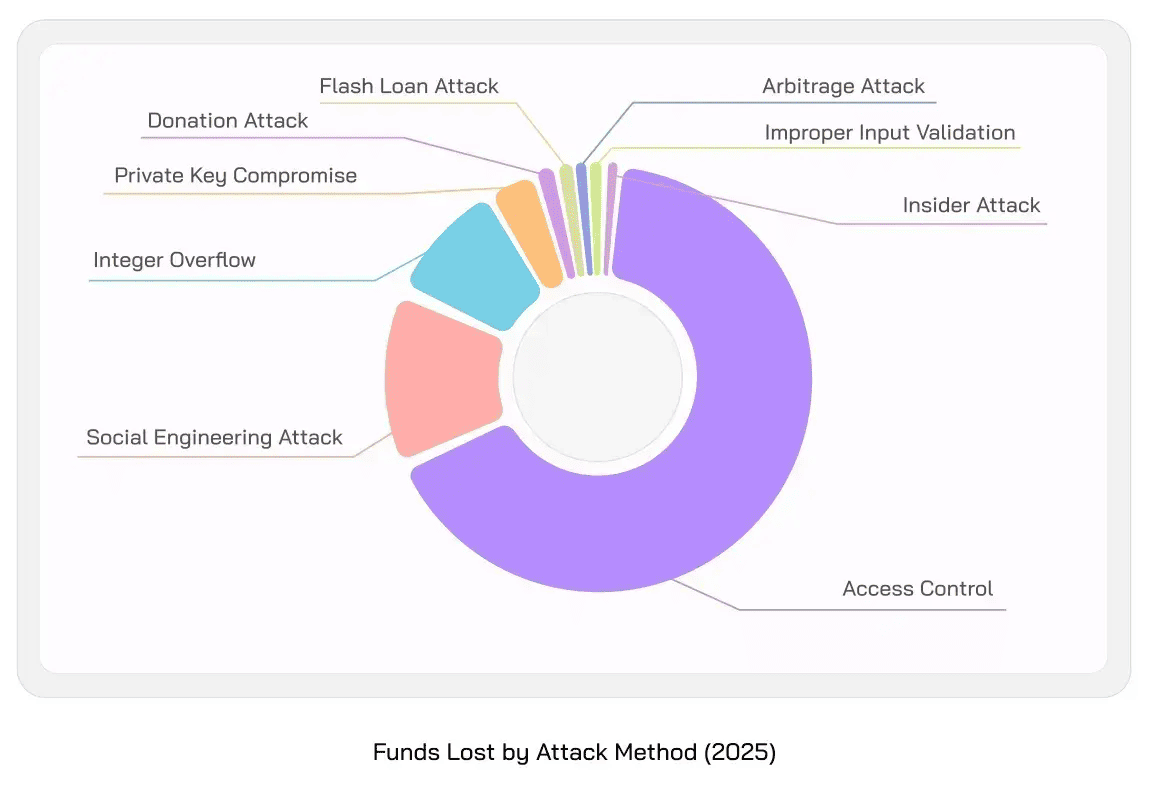
Social engineering scams account for 15% of crypto scam losses in H1 2025 | Source: Quill Audits
How a Social Engineering (SE) Scam Works in Practice
1. Preparation: Scammers study their target, often inside Discord, Telegram, or X communities.
2. Infiltration: They impersonate friends, recruiters, or support staff to gain trust.
3. Exploitation: They send a fake “game,” phishing site, or contract approval. You believe it’s safe and interact.
4. Loss: Your wallet is drained, your account compromised, or your personal data stolen.
This bypasses even the best audits because the “bug” isn’t in the code; it’s in human behavior.
Why Should You Care About Social Engineering Attacks?
Social-engineering scams are now one of the largest sources of crypto losses in 2025. As per Quill Audits, $340M was stolen through social-engineering vectors in H1 2025, part of more than $2.3B lost across hacks and exploits.
Phishing and social engineering remain dominant attack routes, consistently topping incident reports from security firms.
Darktrace researchers have tracked still-active campaigns where scammers build entire fake-company ecosystems, complete with websites, GitHub repos, and Notion pages, to distribute wallet-stealing malware like Atomic Stealer and Realst.
In a bull market, scammers scale fast. With crypto transactions irreversible, a single click or blind signature can mean losing everything, making social-engineering scams one of the most urgent risks for traders and investors in 2025.
The Top 10 Social Engineering Scams to Stay Safe From
As the 2025 bull run accelerates, scammers are scaling up too, using Discord traps, fake startups, deepfakes, and blind-signing tricks to steal millions. Below are the ten most common social-engineering scams you need to know, how they work, and why they’re dangerous.
1. “Try My Game” Discord/Steam Lures (Wallet-Stealer Installers)
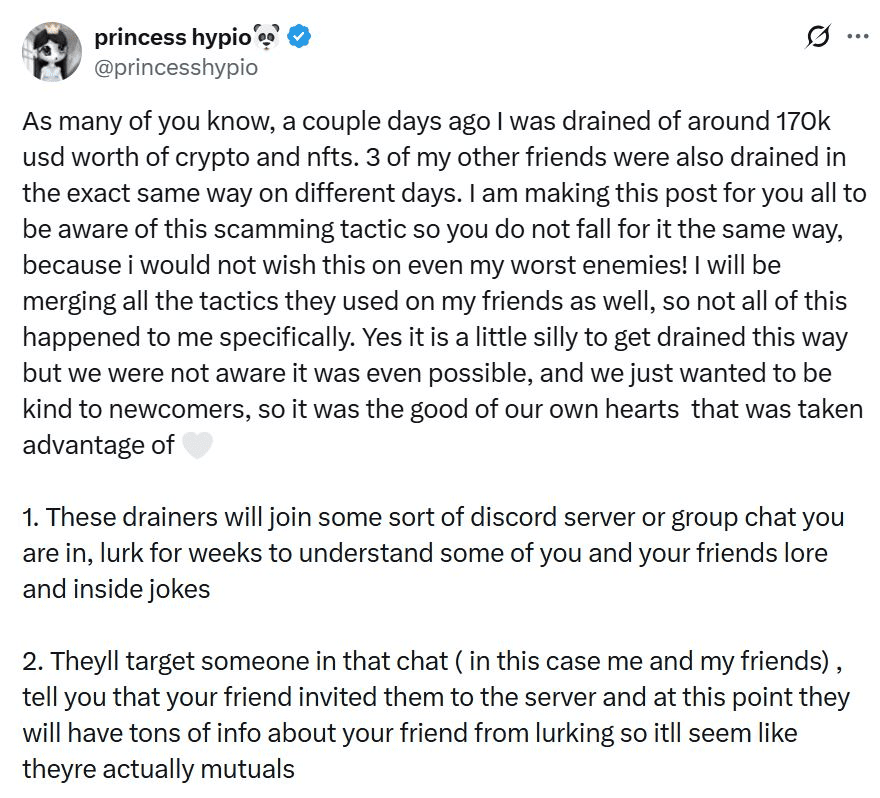
Description of a Discord-based social engineering attack | Source: Cointelegraph
Attackers often infiltrate Discord gaming or crypto servers, posing as friendly community members. After building trust, they send a “playtest” or “try my game” link, sometimes hosted on Steam or a fake file server. Once installed, the program silently drops malware designed to steal wallet credentials, session cookies, and Discord logins, giving scammers full access to both assets and accounts.
A real-world case shows how costly this can be. In August 2025, NFT artist Princess Hypio lost around $170,000 in tokens and NFTs after accepting a Steam-linked “game build” from someone she thought was a friend. Security researchers stress that these scams succeed because they don’t attack the blockchain—they exploit human trust and curiosity in community spaces.
To protect yourself, watch for red flags like offers to “gift you a game,” mutual-friend name-drops, or captchas/“Cloudflare checks” before downloads. Keep gaming and wallet activities on separate devices, never run unsigned or unverified files, and double-check identities using a second channel (like Telegram or phone). A simple pause before clicking can prevent a total wallet drain.
2. Fake AI/Gaming/Web3 Startups (Notion/GitHub/Medium/X Fabrications)
Example of a fake startup social engineering scam | Source: Darktrace
Scammers increasingly pose as AI, gaming, or Web3 startups to trick crypto users. They build professional-looking websites, publish whitepapers on Notion, and upload fake GitHub repos that appear active. Victims are then approached via X, Discord, or Telegram with invitations to “test” new software or join beta programs. Once installed, the app drops info-stealers that scrape browser data, seed phrases, and wallet files from both Windows and macOS devices.
Some of these fake companies go to great lengths for legitimacy. Darktrace researchers flagged groups using stolen code-signing certificates so malware passes system checks, while others operated verified X accounts hijacked from real users to look authentic. Campaigns like “Pollens AI” and “Eternal Decay” even staged fake investor lists and conference photos to boost credibility.
Practical defense comes down to skepticism. Watch for red flags like glossy branding with little working code, mismatched registration info, or cloned assets across multiple “startups.” Always assume unsolicited software is hostile until proven safe. Keep hot wallets empty, rely on hardware wallets with clear-signing prompts, and separate work/test environments from devices used to manage crypto funds.
3. Blind-Signing & Approval-Phishing (Fake Front-ends/Drainers)
One of the fastest-growing scams in 2025 is blind-signing and approval phishing. Attackers clone popular dApps, exchanges, or airdrop claim pages and promote them through sponsored ads, Discord drops, or Telegram groups. When a user clicks “Approve” in their wallet, they unknowingly grant the attacker unlimited token spending rights, allowing their entire balance to be drained in seconds. QuillAudits estimates this attack vector surged in H1 2025, racking up hundreds of millions in losses across
Ethereum,
Solana, and
TON.
These scams work because the wallet prompts look routine. Many users don’t realize that a single approval can cover far more than the small transfer they expect. Red flags include new or unfamiliar websites asking for maximum allowance, wallet signatures tied to unknown contracts, or banners pressuring you with “claim now” or “airdrop ends in minutes.” Even seasoned traders have fallen victim when rushing through approvals.
The safest defense is building habits around verification and revocation. Always inspect what the wallet approval is granting before you click, and run allowance revoker tools like Revoke.cash or Etherscan Token Approval Checker regularly. For bigger trades or claims, stick to a hardware wallet with clear-signing, so you can see exactly what’s being approved. Treat every “Approve” button like a contract; it could expose your entire wallet if you don’t check carefully.
4. Business Email Compromise (BEC) and Executive Impersonation
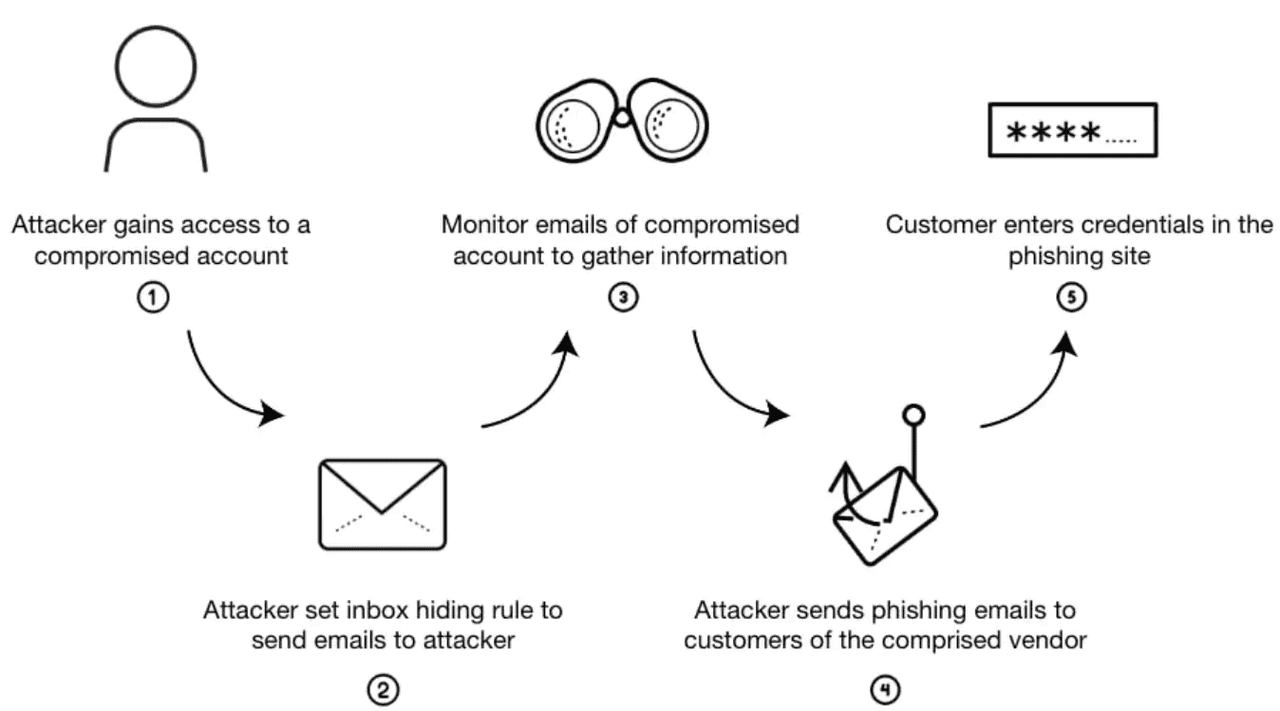
How a business email compromise (BEC) scam works | Source: Palo Alto Networks
Business Email Compromise (BEC) and executive impersonation scams are on the rise in crypto firms during the 2025 bull run. Attackers craft emails or texts that look like they’re from founders, CFOs, or even outside counsel. Instead of sending links or malware, they use plain text instructions like “urgent transfer to this temporary wallet.” Because the messages look routine and contain no malicious attachments, they often slip past spam filters.
These scams thrive on pressure and authority. The attacker usually adds urgency (“funds must be sent today”) or secrecy (“don’t tell anyone until this deal closes”) to push staff into skipping normal checks. Red flags include sudden wallet address changes, payment requests outside the usual process, or instructions that bypass normal accounting workflows. In some high-profile cases, a single convincing message has led to millions in stolen crypto.
The 2025 Bybit hack is a high-profile case: North Korea’s Lazarus Group used social engineering to infiltrate a trusted third-party developer and steal US$1.5 billion in crypto. This shows how even well-protected exchanges can be compromised through human error.
The best protection is process discipline. Always verify new payout addresses through a callback on a verified number or secure channel, never via the same email thread. Require multi-person approval for large transfers so no single employee can act on pressure alone. Training finance and operations teams to recognize social-engineering language is just as critical as running firewalls or audits.
5. Fake Recruiters and “Assessment Tests”
Fake recruiter scams are becoming a favorite tactic in the 2025 bull market, especially as crypto firms rush to hire talent. Attackers pose as HR managers or headhunters, reaching out via LinkedIn, Telegram, or email with offers for high-paying roles. Once trust is established, they send “technical assessments” or “Zoom plug-ins” that secretly install keyloggers, clipboard hijackers, or wallet stealers. Security analysts have even traced some campaigns back to state-backed groups targeting developers.
The danger is that these attacks are tailored to look professional. Victims often receive files in password-protected ZIPs (to bypass security scanners) and are asked to disable antivirus tools “for compatibility.” Others are asked to install meeting software or time trackers that look legitimate but are actually malware. Because the scam mimics real hiring processes, even seasoned developers can be tricked.
The July 2025 CoinDCX heist is an example of this type of social engineering attack. Hackers posing as recruiters lured a company engineer into taking bogus freelance gigs, convincing him to install malware on his office laptop. Within hours, attackers drained $44 million from a liquidity wallet. This shows how recruitment-based scams can compromise even large exchanges when employees are targeted at the desktop level.
To protect yourself, treat every unsolicited recruiter message with caution. Only run assessments in disposable sandboxes or virtual machines where no private data or wallets are stored. Never manage your crypto wallets on the same device used for unverified files. Confirm job offers directly with the company’s official careers page or HR team before downloading anything. A few extra checks can save both your career reputation and your crypto.
6. AI-Powered Deepfake Voice/Video and “Emergency” Payment Scenarios
Deepfake scams are surging in 2025 as AI tools make it easy to mimic voices and even live video feeds. Attackers clone a colleague, boss, or family member, then push for urgent actions, like transferring crypto to a “safe wallet” or reading out a one-time password. Because the voice and face feel familiar, many victims act without hesitation.
The trick lies in the urgency and isolation. The fake caller often claims something time-sensitive, “funds must move within minutes” or “we’re locked out unless you act now.” They’ll also avoid switching to official corporate channels or video tools with stronger verification. The goal is to keep you pressured and cut off from normal checks.
To stay safe, adopt a “don’t trust, verify” policy. Always confirm sensitive requests through a second channel, like calling back on a saved number or checking with another team member. For high-value transfers, use callback codes or pre-set “safe words” that only your team knows. This simple habit can stop even the most convincing AI impersonations.
7. SEO/Ad Poisoning and Watering-Hole Pages
Example of an SEO poisoning attack | Source: Hunt.io
SEO and ad poisoning scams trick users by making malicious sites appear at the top of Google or social media searches. Scammers buy ads or use black-hat SEO to rank pages for hot keywords like “wallet airdrop,” “claim rewards,” or “new token launch.” Some even compromise legitimate blogs or community pages, injecting malicious scripts, fake claim buttons, or trojan installers. To an unsuspecting trader, these sites look identical to trusted platforms.
The danger is that these pages are often timely and convincing. During hyped events like token airdrops or presales, a quick Google search may lead directly to a fake claim page. Victims connect their wallets, sign approvals, and instantly lose funds. Subtle clues, like misspelled domains (binqX.com instead of BingX.com) or odd domain extensions, are usually the only giveaways.
To stay safe, never rely on search results or ads when accessing crypto sites. Instead, type URLs manually or save them as bookmarks after verifying authenticity. Double-check links shared in Discord, Telegram, or X before clicking. If in doubt, confirm the official site from BingX announcements or project documentation. This simple discipline prevents most SEO-poisoning and watering-hole traps.
8. Address Poisoning in Busy Wallets
Address poisoning scams target busy traders who frequently copy-paste wallet addresses. Attackers send zero-value “dust” transactions from addresses that look nearly identical to a real contact’s wallet, often with the same first and last few characters. Later, when the victim goes to send funds, they may accidentally copy the fake address from their transaction history, unknowingly sending assets straight to the scammer.
This tactic works because most wallets only show the first and last characters of an address, creating a false sense of recognition. In the rush of trading or transferring during a bull run, users often skip full verification. Even seasoned investors have lost thousands by sending tokens to a poisoned address that looked familiar but was never actually saved.
To stay safe, never rely solely on history or partial matches when copying addresses. Use wallet features like address whitelists, double-check the entire string, or adopt naming services such as
ENS (Ethereum Name Service) or TON DNS for easier human-readable identifiers. Treat every new or unexpected “dust” transfer in your history as a red flag; it may be a setup for a much bigger loss.
9. Quid-Pro-Quo “Tech Support” and Scareware
Tech support scams exploit people’s trust in authority. Attackers pose as IT staff, security vendors, or even exchange or wallet support agents. They contact victims claiming to fix a problem or provide an urgent “upgrade,” then pressure them to install time trackers, antivirus, or patches. These files are actually wallet stealers or remote-access trojans that hand over full control of the system. Once inside, scammers can drain wallets, log keystrokes, and copy sensitive files like private keys.
Another common tactic is scareware pop-ups. While browsing, users suddenly see fake alerts such as “Your system is infected, click here to clean it.” These warnings mimic Windows or macOS notifications and push downloads that look legitimate. Victims install the “fix,” which secretly logs credentials, hijacks clipboards, or injects wallet drainers. The urgency of the message is designed to bypass logical thinking and push users into action.
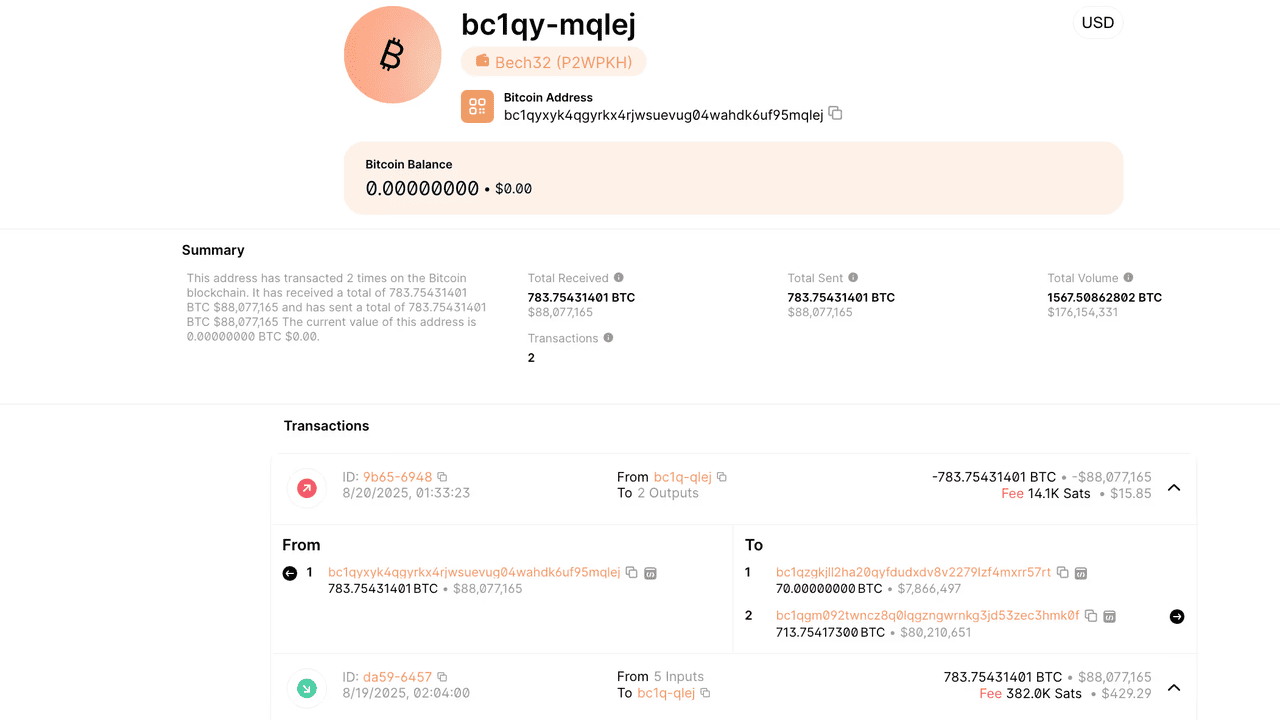
Bitcoin wallet drained of over $91 million in a fake tech support social engineering scam | Source: CoinDesk
The risks are very real: on Aug. 19, 2025, a victim lost 783 BTC, valued at around $91.4 million, after a fraudster impersonated a hardware wallet support agent and tricked them into handing over wallet credentials. The stolen funds were quickly funneled through Wasabi Wallet to hide the trail. This incident, uncovered by blockchain sleuth ZachXBT, highlights how a single moment of misplaced trust can lead to catastrophic losses. To stay safe, only download software from official vendor channels, never grant remote access while managing wallets, and keep wallet activities separate from general browsing.
10. Community Takeovers & Compromised Mod Accounts
Community takeover scams target the places where crypto users feel safest, such as Discord, Telegram, and X groups. Attackers hijack the accounts of long-standing moderators or even verified project reps, then post urgent messages like “migrate your tokens now” or “claim your airdrop today.” Because these posts come from trusted insiders, victims are more likely to click without hesitation.
Some campaigns go further, staging legitimacy by using altered event photos, fake investor announcements, or cloned websites to back the narrative. In 2025, several Telegram communities reported sudden moderator takeovers that spread malicious “claim” links, tricking users into signing wallet-draining contracts within minutes of the posts going live. The combination of trust and urgency makes this one of the hardest scams to spot in real time.
To protect yourself, always cross-check announcements across at least two official channels, such as the project’s website and verified X account. Be cautious of posts linking to brand-new domains, even if they come from familiar names. As a rule of thumb, treat any “migration” or “airdrop claim” notice as high risk by default and verify before interacting. A few extra minutes of caution can prevent irreversible wallet drains.
How to Protect Yourself From Social Engineering Attacks
Scams scale fastest during hype cycles—these five habits will help you stay one step ahead.
1. Separate and Secure Devices: Keep wallets on a dedicated device with a hardware wallet, and use a sandbox/VM if you must open unknown files. Never mix gaming, work, and wallet management.
2. Control What You Sign: Read every wallet prompt, cap token allowances, and run monthly approval reviews with tools like Revoke.cash. Blind-signing is how most drains happen.
3. Verify Before You Act: Never trust the same channel that made the request. Confirm fund transfers or address changes via saved contacts, ticketing systems, or official announcements, and not DMs.
4. Stick to Trusted Channels: Bookmark official URLs, avoid sponsored “claim” links, disable random DMs, and assume unsolicited “friends” could be setups. Use multi-sig and dual control for large transfers.
5. Strengthen Basics and Have a Plan: Enable MFA, use a password manager, and keep software updated. Train teams to spot urgency/authority pressure tactics, and prepare an incident plan to revoke approvals and file reports immediately.
How BingX Helps You Reduce Social Engineering Risks
BingX gives you multiple built-in protections to trade with confidence. You can enable
2FA (two-factor authentication),
anti-phishing codes, and withdrawal whitelists to block unauthorized access. The BingX Academy also provides up-to-date scam alerts and step-by-step security guides, helping you stay ahead of new threats in the market. If something feels off, BingX support is available 24/7; you can file a case with your order IDs, transaction hashes, and screenshots for immediate assistance.
However, no exchange can protect funds you willingly approve of a malicious contract or send off-platform. The strongest defense is your behavior: don’t install unverified software, don’t blind-sign wallet prompts, and don’t let urgency override caution. By combining BingX’s safeguards with smart habits, you can keep your assets safer during the bull run.
Conclusion
The 2025 bull run is creating huge opportunities in crypto, but it’s also amplifying the scale and sophistication of social-engineering scams. From Discord “game” lures to fake startups, deepfakes, and approval phishing, attackers are constantly evolving their playbook to exploit trust, urgency, and human error.
Staying safe requires a balance of platform protections and personal discipline. BingX provides tools like 2FA, withdrawal whitelists, and an education hub on
BingX Academy to strengthen your defenses, but the final responsibility lies with you. Always verify requests, avoid blind-signing, and treat unsolicited offers with caution.
Remember: Crypto transactions are irreversible, and a single lapse can mean permanent losses. Staying alert is your best protection in the bull market ahead.
Related Reading
FAQs on Social Engineering Scams in Crypto
1. What is the hottest social-engineering crypto scam in 2025?
Discord-based “try my game” lures and fake startup downloads are the hottest vectors this cycle; both deliver wallet-stealers under a friendly pretext.
2. Why do social engineering scams bypass audits?
They target people, not smart contracts, no code exploit required. A single rushed approval or unsafe download is enough.
3. How do I spot approval-phishing fast?
Look for requests to grant unlimited spend to unfamiliar contracts and hyped “claim now” pages. Revoke old allowances regularly.
4. Are deepfake scams really a crypto risk?
Yes, AI voice/video clones are used to rush payments or share OTPs. Always verify via a saved contact on a second channel.
5. What should I do right after a suspected social engineering compromise?
Disconnect wallet, revoke approvals, move remaining assets to a clean hardware wallet, change passwords/2FA, and file reports (plus contact relevant platforms).